How to detect and patch Shellshock vulnerability in bash
Last updated on September 27, 2014 by Gabriel Cánepa
bash Shellshock bug, and how to protect my Linux server against the Shellshock exploit.On September 24, 2014, a bash vulnerability nicknamed "Shellshock" (aka "Bashdoor" or "Bash bug") was discovered by a security researcher named Stephane Chazelas. This flaw, if exploited, allows a remote attacker to run arbitrary code by exporting function definitions inside specially crafted environment variables before calling the shell. Then the code inside these functions can get executed as soon as bash is invoked.
Note that Shellshock affects bash versions 1.14 through 4.3 (current), and although at the time of this writing no definitive and complete fix for this vulnerability has been found, and major Linux distributors (Debian, Red Hat, CentOS, Ubuntu, and Novell/Suse) have released patches that address the bugs related to it (CVE-2014-6271 and CVE-2014-7169), and recommended updating bash as soon as possible, and continuing to check for updates over the next several days:
Test for Shellshock Bug
To check if your Linux system is vulnerable to Shellshock bug, type the following command in a terminal.
$ env x='() { :;}; echo "Your bash version is vulnerable"' bash -c "echo This is a test"
If your Linux system is exposed to Shellshock exploit, the output of the command will be:
Your bash version is vulnerable This is a test
In the above command, an environment variable called x is made available to the user environment. It does not contain a value as we know it (but a dummy function definition) followed by an arbitrary command (in red), which will be executed before bash is called later on.
Apply Fix for Shellshock Bug
You can install the newly released patch for bash as follows.
On Debian and Derivatives:
# aptitude update && aptitude safe-upgrade bash
On Red Hat-based Distributions:
# yum update bash
Before Patch:
Debian:

CentOS:
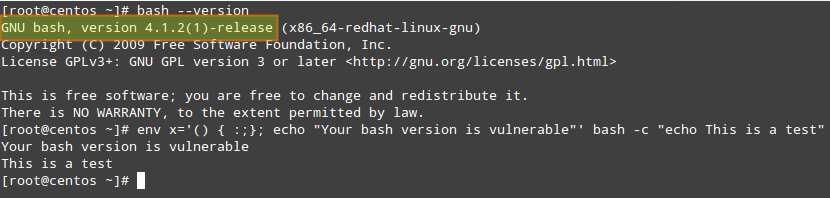
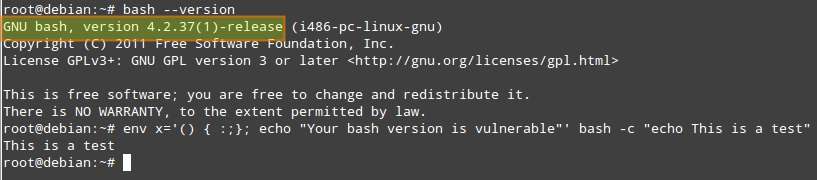
After Patch:
Debian:
CentOS:
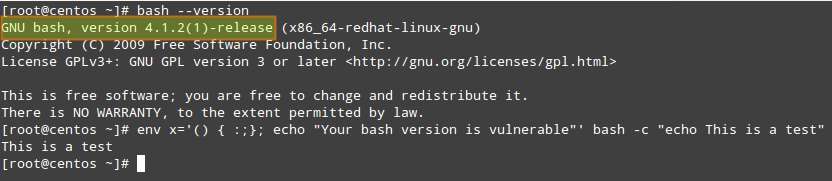
Note that the version has not changed in each chosen distribution before and after installing the patch - but you can verify that it has been installed by observing the behavior of the update commands (most likely you will be asked beforehand in order to confirm the installation).
If for some reason you can't install the patch, or if your distribution has not yet released one, it is recommended to use another shell until a fix comes up.
Support Xmodulo
This website is made possible by minimal ads and your gracious donation via PayPal or credit card
Please note that this article is published by Xmodulo.com under a Creative Commons Attribution-ShareAlike 3.0 Unported License. If you would like to use the whole or any part of this article, you need to cite this web page at Xmodulo.com as the original source.
Xmodulo © 2021 ‒ About ‒ Write for Us ‒ Feed ‒ Powered by DigitalOcean

